Physical Unclonable Function
Jul 2023
An FPGA based framework for an AES secret key generator using a Ring Oscillator Physical Unclonable Function that reliably generates unique and unpredictable 128-bit AES keys
- FPGA
- Security
- Master
This project is part of the course Dependable Computing Systems of my master Embedded Systems at the University of Twente. It has been developed in collaboration with Marten Trip and Jasper Vinkenvleugel.
Our goal was to design an AES secret key generator using a Physical Unclonable Function implemented on an FPGA. A Physical Unclonable Function, or PUF for short, is a cryptographic primitive that makes use of variations in the manufacturing process of electronic chips to act as a fingerprint for a specific device. The PUF needs to give a reliable response for the same request called a challenge. Ideally this response should be unique for every chip the PUF is implemented on. Therefore, the AES key that is generated for a specific challenge is evaluated on three metrics:
- uniqueness: the ability of one PUF to have uniquely distinguishable behavior compared to the same PUF structure implemented on different chips. Computed using inter-chip Hamming Distance, which in the ideal case is 50%
- reliability: the ability of the PUF to generate a consistent response R for a challenge C, regardless of any changes in the conditions of the environment. Computed using intra-chip Hamming Distance, which in the ideal case is 100%
- uniformity: the ability of the PUF to generate “unpredictable” responses, defined as the proportion of 0's and 1's of the response. Computed using the average Hamming Weight, which in the ideal case is 50%
A method to implement a PUF is to use a looping chain of an odd number of inverters to create a ring oscillator. The frequency of the oscillator will be determined by the impurities of the position of the chip it is implemented on. A comparison of two oscillators should always give the same answer for the same (location on the) chip, but a different answer when the same oscillators are implemented on a differnt chip. This gives one challenge response pair (CRP), thus a one bit fingerprint. To support more device fingerprints, more oscillators can be added.
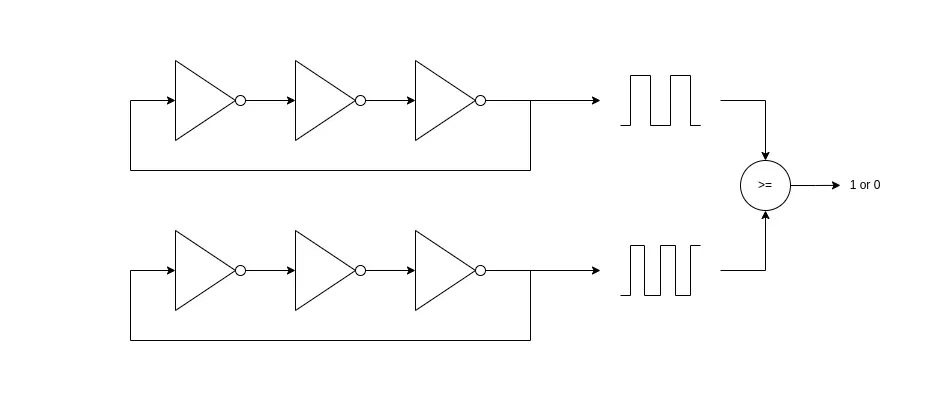
PUF based on ring oscillators. The frequency of the oscillators is determined by the impurities of the silicon of the specific location on the chip where they are located. Therefore, if it is implemented on a different chip or on a different location on the chip, the frequencies will be different and the result of the oscillator comparison will change based on which you test. When scaled up, it will act as a fingerprint for the specific device
Our framework allows fine scaling controls of the PUF to fit the needs of the design in three levels of modularity: RO block, RO PUF block, nPUF block. The ring oscillator in the RO blocks have a variable amount of inverters that control the frequency, and multiple of these can be implemented in the RO PUF block to size the number of unique fingerprints. The nPUF block implements multiple RO PUF blocks to generate multiple responses for the same challenge at the same time. This allows us to generate an AES keys faster or have additional logic in the key generation algorithm for extra security measures.
We implemented a PUF with 4 RO PUF blocks, each containing 1024 ROs of 5 inverters on four AMD Kria KV260 FPGA boards. This setup shows a 49.72% uniqueness, a 99.62% reliability and 49.48% uniformity, where the reliability uses two measurements of the same chip at a high and low temperature. From these results we can see that, although for a small sample size, our framework operates close to the ideal case for a PUF (50% uniqueness, 100% reliability, 50% uniformity).
For this project, I took the role as system architect, where I was mainly responsible for the design and development the modular architecture of the framework of the PUF. My teammates took responsibility of figuring out the VHDL constraint file to give us control over the placement of the RO blocks, to get a repeatable framework as well as taking care of the Jupyter Notebook running on the on-chip ARM core that controls the PUF. Before I started this project I had only an elementary understanding of FPGAs and VHDL, but this project allowed me to grow my understanding of FPGAs and VHDL development.
Credits cover image: servethehome.com